Using GUI:Open "Active Directory Users and Computers" from the Administrative Tools menu or by running "dsa.msc" command.Right-click on the domain and select "Operations Masters" to view the current role holders.Step 3: Verifying Role TransferUsing PowerShell:Launch PowerShell with administrative pr...
In the field of web security, the ability to handle a variety of certificate formats is important. Sometimes, you may need to convert a PFX (Personal Information Exchange) certificate to other commonly used formats like CER, CRT, and PEM. In this blog post, we will explore the step-by-step process f...
Changing the Remote Desktop Protocol (RDP) port number is a security measure that can help protect your system from unauthorized access. The default RDP port is 3389, and many attackers know about it. Changing the port number adds an extra layer of security, making it more difficult for automated to...
In the field of secure networking, it is important to have a robust and flexible VPN solution. pfSense, a powerful open-source firewall and router platform, provides an excellent foundation for implementing OpenVPN. In this step-by-step guide, we'll walk you through the process of setting up OpenVPN...
In an era where digital security is of utmost importance, organizations and individuals alike are looking for advanced solutions to protect sensitive information. One such strong security measure is the SafeNet 3300 Passcode Device. This state-of-the-art device is designed to enhance security pr...
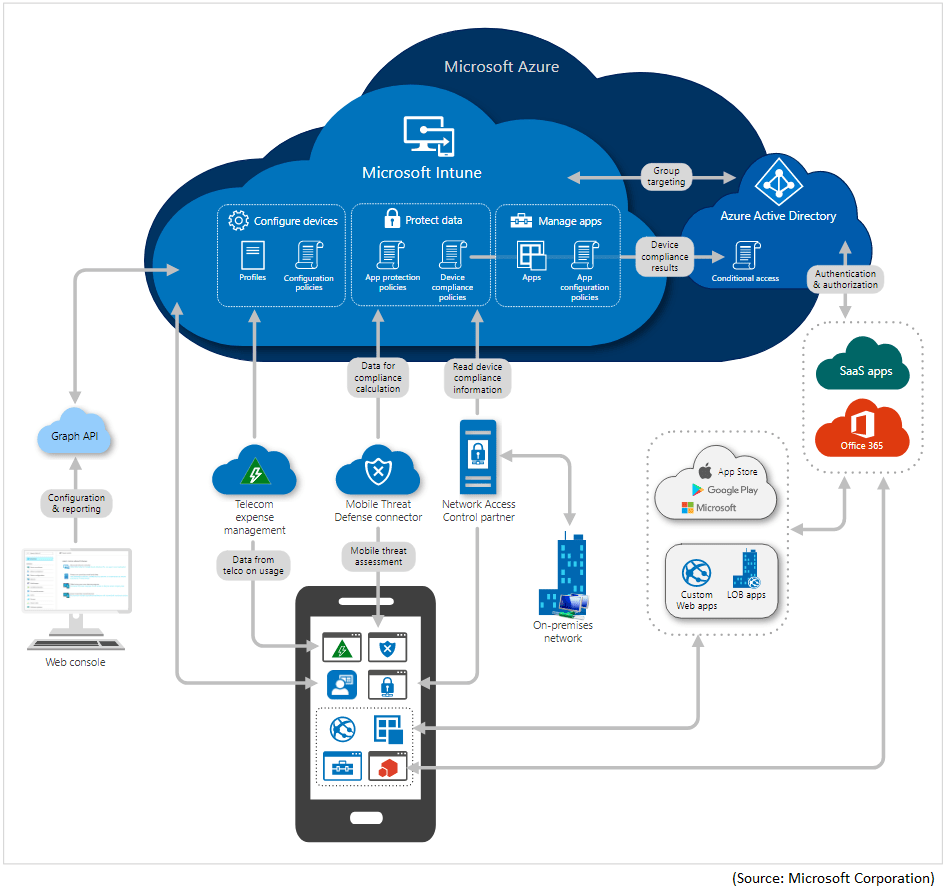
Office 365 MDM vs Microsoft IntuneMobile Device Management (MDM) is a useful option for a large number of organizations that want to manage their mobile devices securely (Android, iOS, and Windows).Fortunately, many subscriptions to Office 365 include MDM. You can use Microsoft Intune to manage y...
1 - 6 of ( 7 ) records